IT Services
We offer Network penetration testing and vulnerability assessment for corporates to secure their perimeter of digital premises. These top-notch services are mainly availed by the banking and finance sector, healthcare and investment sectors.
We also offer end to end design and solutions for secure network architecture to keep the unwanted elements at bay. The offered services include complete lifecycle of the IT Security project including but not limited to presales, design, implementation, commissioning and support.

Cybersecurity Consulting Services
- Security Strategy and Planning: Developing customized cybersecurity strategies aligned with clients’ business objectives.
- Providing response and forensic investigation services in the event of a cybersecurity incident, such as data breaches, malware attacks etc.
- Helping clients navigate cybersecurity regulations and compliance requirements, such as PIPEDA and industry-specific standards like PCI DSS or HIPAA.
- Educating employees about cybersecurity best practices to reduce the risk of human error and enhance overall security.
Safeguarding Measures
Oftentimes, hackers attempt to gain unauthorized access by exploiting vulnerabilities in the system, and steal customer information or commandeer operations.
Strong authentication is critical for ensuring no unauthorized access. Multi-factor Authentication (MFA) and biometrics can add a layer of security and verification. This ensures that only authorized users and individuals have access to sensitive information.
Apart from ensuring there isn’t any unauthorized access, as well as adhering to Data Privacy Protocols, it’s important for companies to strengthen their infrastructure and network security to defend itself against cyber threats. We can do so by adhering to secure coding and software development practices such as input validation, output encoding, and proper error handling. With the help of regular security testing (such as the Vulnerability Assessment & Penetration Testing), our company can help identify vulnerabilities and weaknesses in applications.
Protecting customers’ data and privacy are our top priority, which is why we strictly adhere to data privacy regulations such as the General Data Protection Regulation (GDPR) in order to maintain customer trust and reliability. Customer trust builds the foundation of any successful company. It is vital that customers feel that their data is in safe hands and that the services they utilize are reliable. “Tokenization and Encryption” techniques can be implemented to safeguard both data-at-rest and data-in-transit. Access controls must also be put in place to maintain data integrity and clearance.
IT Services
The following are the Cybersecurity Software Solutions and Services, which G-Fin Tech Solutions will provide.
Financial Services Industry
The financial services industry offers banking, investments, insurance, and wealth management for individuals and businesses.
Healthcare Sector
The healthcare sector provides medical services, research, and products to improve and maintain health.
Government and Defense Organizations
Government and defense organizations manage public administration, national security, and defense operations to ensure safety and stability.
Critical Infrastructure providers (Utilities, Energy, Telecom etc.)
Critical infrastructure providers, such as utilities, energy, and telecom, ensure essential services and support the functioning of society.
Retail and E-commerce businesses
Retail and e-commerce businesses sell products directly to consumers, both in physical stores and online platforms.
Technology and software companies
Technology and software companies develop and provide digital solutions, products, and services to enhance business operations and consumer experiences.
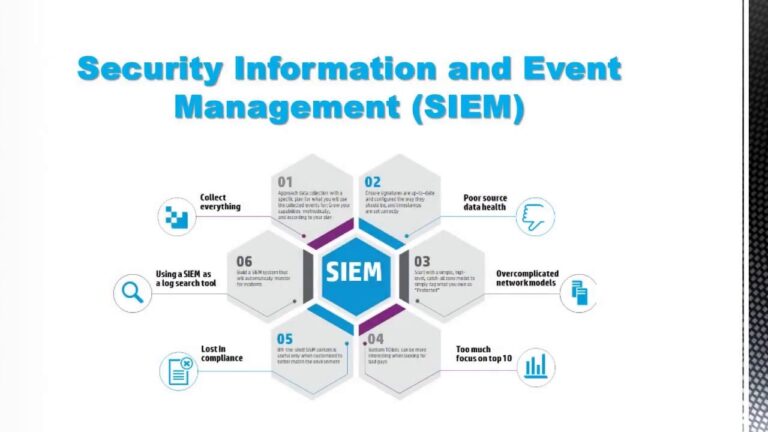
Security Information and Event Management (SIEM) Solutions
- Incident Response Orchestration
- Threat Detection Correlation
- Forensic Analysis and Investigation
- Real Time Monitoring
Identity and Access Management (IAM) Solutions
- Authentication and Authorization
- Identity Governance and Administration (IGA)
- Identity Federation and Single Sign-on (SSO)
- Multi Factor Authentication (MFA)

Encryption and Data Protection Solutions
- Database Encryption
- Application-Level Encryption
- Tokenization and Masking
- Access Controls and Data Governance
Incident Response and Forensics Solutions
- Incident detection
- Post Incident Analysis and Reporting
- Threat Hunting
- Incident Triage and Prioritization


Cryptocurrency
- Portfolio Management
- Market Data and Analysis
- Staking and Yield Farming
- Blockchain Explorer
